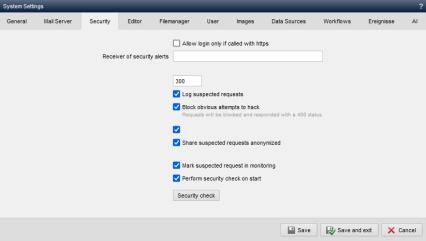
System settings - Security
Global security settings can be made in the 'Security' tab in the system settings.
This currently enables logging and notification of access to the project that is classified as suspicious by the software.
As a rule, these are calls to existing pages, but also pages that do not exist in the project, which are given various URL parameters. These are often paths to open source products for which security vulnerabilities are known and potential attackers "scan" the web for such installations. Attempts are also often made to use URL parameters to uncover vulnerabilities in existing (PHP) pages and then exploit them if necessary.
In all cases, such calls are usually visible in the access logs for the domain of every provider and can be analyzed.
Weblication® makes these calls transparent even without access to the domain's access logs and, depending on the settings, notifies you directly when suspicious accesses are made (E-Mail SecurityAlert). This should enable you to react quickly or faster if necessary.
Operation
'Enable login only via HTTPS':
If this parameter is activated, a login is only possible if the Weblication® CMS software or form login screen was accessed via the https protocol. If the login mask was called up via the http protocol, this is treated as an incorrect login.
Tip: Use an htaccess rule in the top directory level of the domain to ensure that an http call is redirected to https.
Note:
Depending on the server configuration, it can happen that a login does not work when this option is activated and also when https is called up. Possible causes may include proxy settings or missing server variables under PHP.
'Recipient of e-mail warnings':
In this field, you can optionally enter the email address to which an email should be sent if the logging of suspicious access is activated (see below).
These emails are defined in the subject as follows (example):
E-Mail SecurityAlert: http://IhreDomain.tld
You can therefore filter such e-mails directly in IMAP or in the e-mail client via e-mail filters and move them to a mail folder, for example.
The content of such an e-mail lists the following values, if they can be read out:
- IP address
- URL
- referrer
- user
- User type
- User agent string
The URL shows you the suspicious access, i.e. which URL was accessed with which URL parameters. This allows you to determine whether this call really exists in relation to the respective project or whether there is an attempted attack. This assessment must be carried out individually in each case.
Further information and tips can be found in the developer article"Dealing with email warnings".
'Pause between emails in seconds':
In this field, you can optionally enter the number of seconds to wait until another email warning is sent (e.g. 300 for 300 seconds).
The recipient will not receive any further emails until the specified time has elapsed or they open the Security Center.
'Log suspicious access':
If this parameter is activated, URL calls that indicate suspicious activity are logged in daily log files.
'Block obviously malicious access':
If this parameter is activated, accesses that have been classified as malicious accesses are only answered with a status 400 (Invalid request) and are not processed further. There is no warning by e-mail.
This reduces the number of e-mail notifications and still ensures effective action against such requests.
'Block the visitor for 1 to 2 minutes after blocking':
If this parameter is activated, the IP address in question is blocked for 1 to 2 minutes after a malicious access is blocked.
This makes it more difficult for bots to attempt attacks, which carry out a large number of accesses in order to search for vulnerabilities.
'Share suspicious accesses anonymously with the security server':
If this parameter is activated, the URL calls that indicate suspicious activity are also stored on a security server with anonymous data so that they can be evaluated accordingly.
The note text below the description text explains the purpose of this option:
"This function helps us to detect and respond to new threats more quickly. "
'Mark suspicious accesses in monitoring':
If this parameter is activated, URL calls that suggest suspicious activity are marked in server monitoring.
'Show server security check in dashboard':
If this parameter is activated, the security check is displayed in the dashboard. The security check is also carried out each time the backend (personal area) is opened.
For performance reasons, it is best to deactivate this parameter if you are sure that the security checks are positive.
'Server security check':
Clicking on this button opens the Weblication® server security check.
Notes
If you want to allow calls (e.g. from internal or desired IP addresses) that are regarded as suspicious access and may be blocked, you can set a corresponding query via pre.php (e.g. if query on REMOTE_ADDR). Within the query, set the global variable"doNotCheckSuspectLevel" to true:
$GLOBALS['doNotCheckSuspectLevel'] = true;


